AWS: Advanced IAM Permissions
Intro
In our sample application to compare user data we currently are using Lambda functions to store and retrieve data from a DynamoDB table. Currently those Lambda functions have been given IAM roles that provide them with blanket permission to read + write anything from any DynamoDB table. That let's the functions do their job, but it's very bad practice to give such extreme permissions.
What we would like to do is restrict the permissions of these Lambda functions to the scope of what they are intended to do. Such as read or write to one specific table. This is called the Principle of Least Privilege. Let us do that now.
If you are not familiar with the basics of AWS IAM review the introduction here:
Create A New Policy
One of the ways that we can simplify this process is to create a new policy, which we can attach to our Lambda function roles. We want to create a new policy that does the following.
- Applies only to DynamoDB
- Applies only to a specific table
- Allows only specific methods on that table
And we will create two policies, one for reading, and one for writing. To start navigate to IAM > Policies > Create Policy

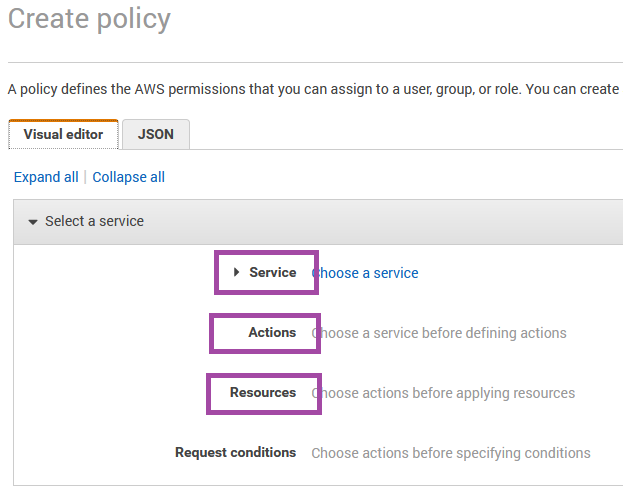
Service refers to all of the AWS microservices. We want to restrict this policy to DynamoDB.
Actions refers to the SDK API methods that we are using in our Lambda functions. Like .putItem for adding new items to the table.
Resources is asking for us to input an ARN (Amazon Resource Name). The ARN is a unique ID for every AWS resource across all AWS accounts. This is where we can specify what DynamoDB table we are targeting. The ARN is available in the table overview tab DynamoDB > Tables > compare-yourself > Overview > Table Details
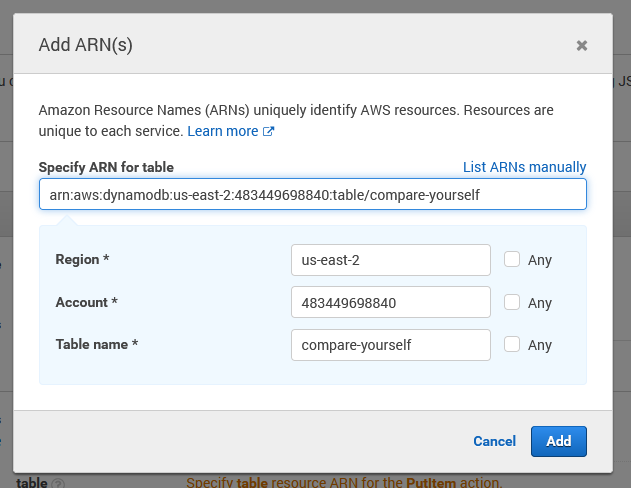
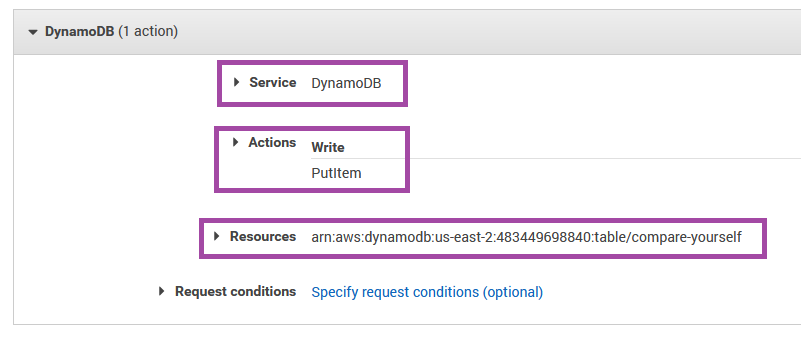
So we simply fill in all those details as we would like.
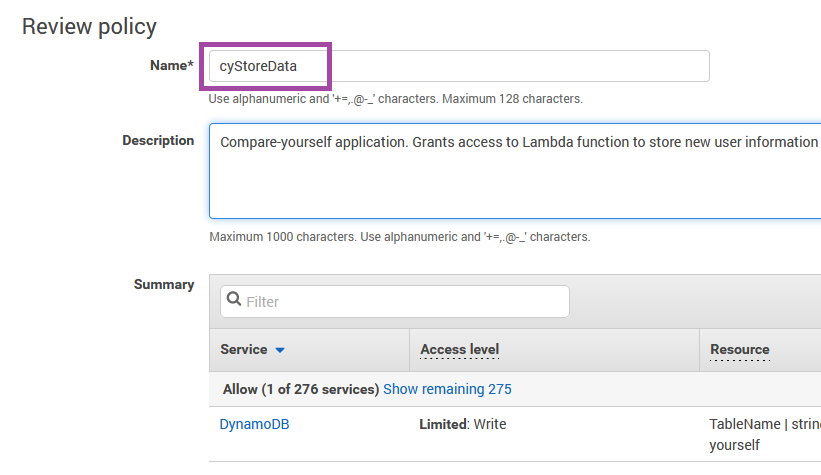
After that you can add an organizational tag, and then you get to name the new policy. So far we have a naming convention for our Lambda functions that start with cy for compare-yourself, so let's continue that convention. In fact since this policy is for one specific function in Lambda called cyStoreData let's just have the policy name match that exactly.
Create New Roles
Now that we have a new targeted policy, let's create a new role that we can attach that policy to.
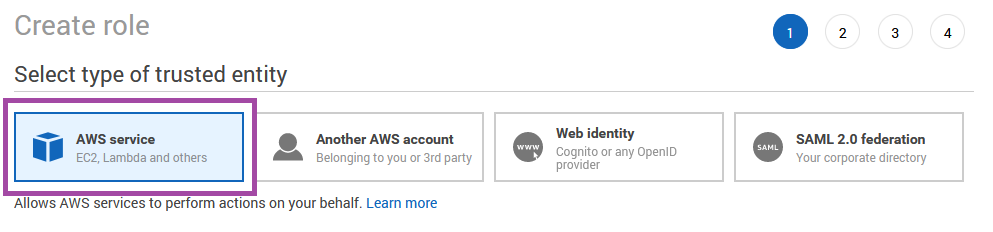
We select the appropriate type of role, and then we can attach the policy that we just created.
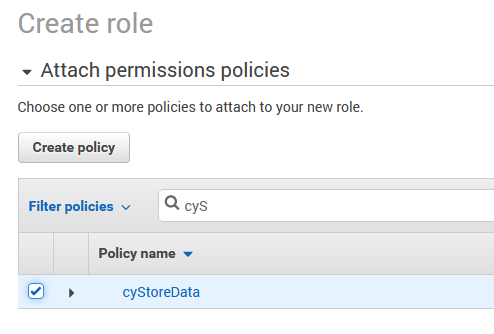
And we will also name that cyStoreData. There only needs to be one role on this Lambda function, and if we need to attach additional policies to that role later we can.
Attach Roles to Lambda Functions
Lastly we can go back to our Lambda function and update the role. When we get there we are reminded that this role should also have access to CloudWatch Logs, which is essential for debugging, so we can then go back and add that policy to the role.
Comments
Recent Work
Basalt
basalt.softwareFree desktop AI Chat client, designed for developers and businesses. Unlocks advanced model settings only available in the API. Includes quality of life features like custom syntax highlighting.
BidBear
bidbear.ioBidbear is a report automation tool. It downloads Amazon Seller and Advertising reports, daily, to a private database. It then merges and formats the data into beautiful, on demand, exportable performance reports.